Android VNC Without root as a PDF document
————————————————————–
Notice: On June 2, 2018 at 11pm eastern time, FB admins blocked me from posting anything within Facebook, therefore i cannot reply or comment toward anything on my own timeline while other people can.
https://brianaberle777.wordpress.com/2018/05/12/facebook-wants-my-account-to-be-hacked/
On June 4 my facebook account is unlocked. If you found me through FB (stands for Fuckin Bitch) please use my email to chat – or contact me. I like cool people writing on my timeline – drop me a line there.
On June 6 im under FB admin attack again, i dont know what you see on my timeline, i verified that you dont see what i put there today. This is the case in the morning of June 6. After only a few hours, they released my account again.
Today June 7 all is normal, in the morning anyhow. Admin vs. Admin – Round 9
Someone give FB a slap for me before i do it myself.
In Silicon valley, Facebook doesnt have friends.
June 8 is looking good.
On June 15 at 2:40 AM Eastern time Facebook admins blocked my account again.
The June 15th block prevents me from posting on my own timeline while all my FB friend are allowed to post on my timeline. I am also prevented fro musing FB messenger to send any messages to FB friends. This censorship is because I just published evidence about Ashe County police and justice system corruption. Facebook does not want their social platform being used for exposing corruption.
LOOK @ what your are not supposed to see.
https://brianaberle777.wordpress.com/2018/05/01/in-and-out-g-shit/
https://brianaberle777.wordpress.com/2018/04/21/obstruction-of-injustice/
————————————————————–
This document is online at: https://brianaberle777.wordpress.com/android-vnc-server-without-root/
In June 2013 Google allowed the VNC Server to be stolen. Google is committing treason to the entire open source community by supporting this violation of GPL. There is a VNCServer in the Google Play store for $7.99 claiming to be the First and Only VNC Server that does not require a device to be rooted. Search for “Android VNC Server without Root”, its all over the Internet.
A little History:
I have been working with VNC source since 2002. I statically linked VNC into an experimental build of my product and showed it to Andy Harter in 2007 for my work on Windows Mobile. He told me that the static link will violate GPL unless my product is also open source. I respect old school net etiquette and responded by putting VNC in its own process.
The source code, when I obtained it from http://code.google.com/p/android–vnc–server was not so simple to build. To start with I needed SVN, The Subversion source control system. After obtaining all the code, it would not build until I obtained, built, and linked the jpeg and zlib libraries, then I edited the makefile to setup the dependent libraries path and file name.
I republished the source code. I rearranged the build so that this VNC Server does not link to any dependent library. The source from the two needed libraries is now included into one project makefile, and its in all in one zip file. The source is clearly split into their respective folders and it is unchanged. Now you can “download and build”. (Install the Android NDK first) This major simplification to the build process will help to advance the code base by simplifying developer adoption. The source code for building android vncserver is included in the attached files. The binary is also included so you don’t need to build it.
Just want to see VNC work without rooting?
One prerequisite is that you install the “Google ADB USB Driver” on your PC that will launch the process on your Android device. There are many places on the internet that will guide you to the drivers.
- You need to enable the ADB interface on your phone/tablet – look under device settings or security settings
- Plug your Android device into your computer by USB cable
- Open a command prompt(Start/Run/Accessories/Cmd) to the folder where you have the file androidvncserver.
- adb start-server
- adb push androidvncserver /data/local
- adb shell chmod 777 /data/local/androidvncserver
- adb shell /data/local/androidvncserver –t /dev/input/event1 –k /dev/input/event4 &
7. adb shell /data/local/androidvncserver –t /dev/input/event2 –k /dev/input/event4 &
7. adb shell /data/local/androidvncserver –t /dev/input/event3 –k /dev/input/event4 &
———–Find your touch input—————————-^
Step 7 will vary from device to device.
That’s it.
I tested with several VNC viewers. TightVNC works best with the Android VNC Server. Download it for free from http://www.tightvnc.com –only download the viewer. The VNC Server (on your phone) is on port 5901 because 5900 is locked by the OS.
I am using Xfer to view the process list on the device – In this case an LG Optimus. However, the VNC Server has nothing to do with Xfer. Xfer is not required to achieve “VNC Server without root”.
Notice in the process list, under Handles, the androidvncserver process is ‘shell’, this “shell” is the process permission that allows the system files to be accessed with elevated permissions. Your VNC viewer can connect directly if you can route directly over TCP. If your computer can ‘ping’ the phone (if it is on the same sub-net) then you can connect directly from a VNC Viewer to 123.123.123.123::5901 (where 123.123.123.123 is your ip address). If the phone is on another subnet, you need Xfer to tunnel a connection for you. Xfer does encrypt screen data before it is sent over the air.
If you think that VNC Server without Root, is a monumental leap forward in personal technology management, then wrap your mind around this:
The free Xfer Android app allows the device to host any TCP server application on the public Internet. This has been documented in detail in the protocol documentation and it will not be reiterated here. The binaries and documentation for Xfer are here:
https://www.dropbox.com/s/2fw7q4531gdaq0f/Xfer%20Eval.zip?dl=0
The androidvncserver does not encrypt screen data, but if you send it over Xfer, then rest assured that not even the government can see what you are doing. Xfer’s 128 bit encryption uses an additional packet sequence key so that if one packet was cracked (probably months or years too late) even then -the current sequencing scheme would never allow the information to be reused as a valid transaction at the current cipher sequence. The security that Xfer adds is secondary to the new TCP routing capabilities.
This s what it does: Your VNC Client will connect to your computer on port 5900. That connection is tunneled up to a switchboard server on the internet. The Android device must also be able to reach the switchboard server, so it will work whenever the device can browse the internet. The TCP data is sent to the device, decrypted, and forwarded to port 5901. The VNC Server thinks that the VNC Viewer is running on the Android device at 127.0.0.1, when in fact the VNC Client is running on a PC. The VNC Viewer is also unaware of Xfer – connecting at 127.0.0.1 on port 5900.
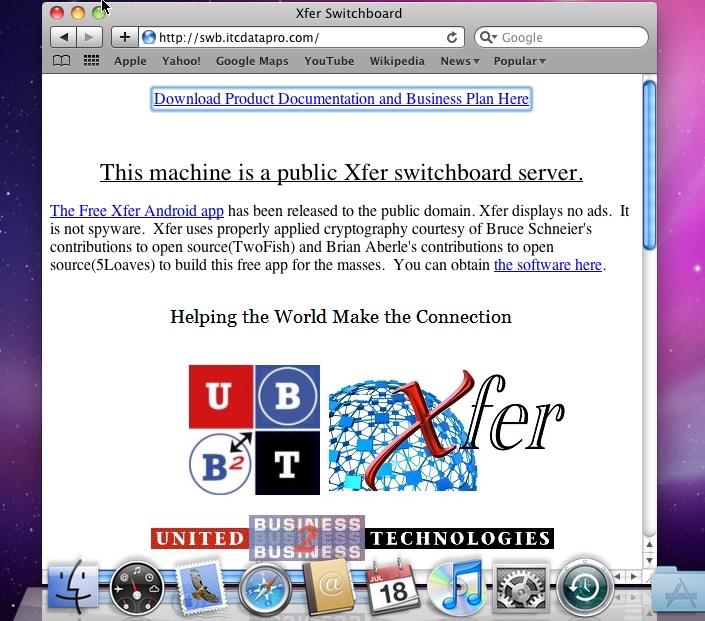
In the image below, notice the connection path in blue at the top left. This VNC session is safely being routed through a public switchboard server that I have setup.
Using the free Xfer Android app, and the free version (aka the evaluation version) of the Windows GUI, you can route the screen data across subnets for free. This is truly a free solution that uses free components.
Xfer adds an essential element to connecting your computer at home/ office to your phone/tablet. This allows you to push pictures and mp3 between your PC and phone/tablet with the internet between them both. Don’t need to go home and plug in wires because the pictures are already there. If your phone/tablet is lost, damaged, or stolen none of the information is lost.
This may help you understand how much the subnet bridging matters:
… and the above image may help you understand what subnet forwarding can do on an unrooted phone.
Google’s been shady and sneaky too. Gmail users have their every word indexed for direct marketing ad delivery, and while direct marketing may not be illegal, some folks don’t like it.
There is nothing Shady and Sneaky about Xfer. Nobody has ever done this for free before. EDI VANS cost money. Search that. That’s where Xfer came from because it is designed for distributed systems integrations. The same technology is needed between your phone and computer that is need for complete B2B. It becomes one system. That is “System Integration” (aka Distributed Computing) the roots of which are in COM and CORBA that were blocked at the firewall because Xfer did not exist at the time. Xfer is the only solution that bridges subnets recursively deep. That means a single connection path may contain multiple switchboard servers in it. This is all documented in detail in the protocol docs.
As for the entire solution being free – It is. The Windows GUI will not allow any connections into your machine unless you “Start the Xfer Server”. You do not need to “Start Xfer Server”, to accomplish everything presented here as a free solution. You can even evaluate setting up your own Switchboard server using the windows GUI, a private switchboard server will be faster than a public server. I will maintain free public switchboard servers. Plural.
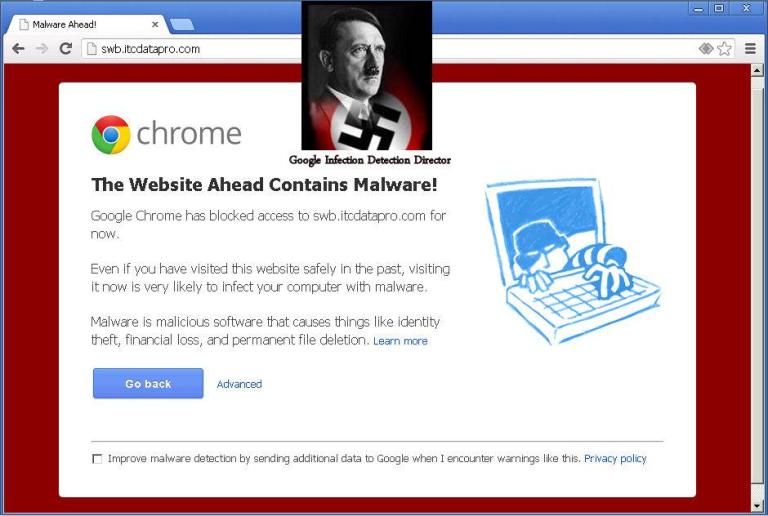
The most disturbing practice of Google is not about what they force you to see, but about what they prevent you from seeing:. An honest web browser displays any HTML document. W3C defined the rules.
IE doesn’t have any problem displaying the HTML and JPG files hosted by the Xfer HTTP Server.
Neither does Netscape(on 64 bit Windows 7).
The newest Firefox is tied into the new Google censorship program: Firefox is a good browser, I hope they fix that.
Thankfully, Apple is not participating in the Google censorship program. As of July 18, 2013 Safari (on Macintosh) looks like this:
And in the next picture you can see Google chrome: (I added the picture at the top of this screenshot)
Yours Truly,
Brian Aberle






Do you know anything about getting this working today on modern versions of android? I’m searching github (google code closed down) and there’s tons of forks there; I’m hoping that there’s one or more than is active and that you can recommend as the original author.
Further, I have no idea how to compile the existing project–Android SDK no longer uses eclipse, it uses Android Studio and gradle, and binaries that worked with older versions of android no longer work (android now requires PIE/PIC binaries)
LikeLike
Maybe you have found a solution by now but I will update my vnc code based on v 3.3.3 with examples for the gradle build because the post about vnc is extremely popular
LikeLike
That would be appreciated. Perhaps you could upload the code to GitHub? I can’t seem to actually find it anymore 😦
LikeLike
Apparently many folks have been hunting the Android VNC Server source. I have my own example application for Android that will work in conjunction with the VNC Server, therefore I added the VNC Server as an example under the Examples/Android folder in the XMLFoundation source distro. http://www.codeproject.com/Articles/37850/XMLFoundation
LikeLiked by 1 person
Hi, this is awesome, but I’m reading that You need adb, in that case, this will not work over public networks right? Am I wrong?
LikeLike
You need to hook the android device to a computer to launch the VNC server process. Once running, anything that can reach the device can connect – if you have cellular data you will have a public IP address and the device can be reached from anywhere. If you are on Wi-Fi you will get an IP address on the local network and the device can be reached from any other device on the same Wi-Fi network – unless you use some kind of network routing solution to access via the internet.
LikeLike
Thanks for this post Brian! Is there any way you can update or elaborate on how to adb push androidvncserver /data/local without rooting?
LikeLike
Root isn’t necessary for adb. You also don’t really even need adb, you can just enable third-party install from developer tools, copy the .apk over, and install it locally. ADB is just easier if you already have your device set up for development.
LikeLike
…Ignore that. I apparently wasn’t paying attention. You could alternatively try opening your terminal app, copying the binary to its private folder (usually ~) and then running it from there, but I have no idea if that would actually work or not.
LikeLike
I suspect that will work if the device is rooted, but when the VNC process captures the screen it must be running as su (superuser or root). When ADB launched the process – it elevated permissions just like root had started the process.
LikeLike
Thanks again Brian, I went one dir lower at /data/local/tmp and it worked. However, I cannot open fb device /dev/graphics/fb0. Did you ever run into that one? Thanks!
LikeLike
Hi, is there a chance to find the code? Would be awesome to try this!!! Google Code url is down 😦
LikeLike
You can now find the VNC server code in the Android examples of XMLFoundation http://www.codeproject.com/Articles/37850/XMLFoundation
LikeLike
hi
I downloaded the binary from https://code.google.com/archive/p/android-vnc-server/downloads .
I copied it in ‘/data/local’ directory and made it an executable.
And then I ran the executable.
I can also connect a VNC viewer from a PC on same network,
The issue is that viewer is showing a blank screen and a ‘x’ for mouse pointer …
regards
Atul
LikeLike
I don’t know for sure what your problem is but I can offer a few ideas:
1.) Check out the July 2016 of http://www.codeproject.com/Articles/37850/XMLFoundation which allows you to build the VNC Server
2.) Try another VNC Viewer. I tried many of them and they all seemed to work a bit different. TightVNC worked the best for me.
LikeLike
Hello and thanks for all this interesting info. I also tried the binary at https://code.google.com/archive/p/android-vnc-server/downloads on my Android 5.1.1 device. It complains saying only PIE code is permitted. I tried an app on Play Store which, I believe, also uses the same binary and it fails the same way. I feel rather stupid because I have looked around the CodeProject page and cannot seem to find the package to download. How do find it? Thanks!
LikeLike
Sorry. You can ignore most of my last comment. I just found the download link right at the top! I am getting too old. I have the zip now. But I thought I read somewhere that the binary was available so I might avoid the build. Or was that only for an older version? Thanks
LikeLike
I have never seen the PIE code error you mentioned – but I expect that others have seen it so your documenting it contributes to this shared knowledge as a whole. The source download from codeproject does not contain the binary executable – only directions to build it yourself. I just posted the androidvncserver binary here: https://www.dropbox.com/s/wo5cz4zjmb70dfp/androidvncserver?dl=0
LikeLike
Thanks for the link to the binary. It does seem like Lollipop changed things (they say for additional security) . Aside from re-building with PIE enabled . It seems that one can replace or patch the linker. I will try the latter 2 options and see what happens. Thanks again for all.
LikeLike
Hi Brian:
The build instructions are great and I’ve built using ndk with no problem, but with a non-rooted device (but yes, with USB Debugging enabled) adb does not have permissions to push to /data/, or /data/local (Android 4.2.2 or 5.1.1) – adb shell also does not have permissions to even ‘ls /data/’.
If use the host linux commands to copy androidvncserver to the mounted android filesystem, I still cannot modify executable permissions.
However, it does appear that I can write to /data/local/tmp (4.2.2 & 5.1.1) , and change permissions there, but when I try to execute with adb shell I get:
(4.2.2) /system/bin/sh: /data/local/tmp/androidvncserver: not executable: magic 7F45
(5.1.1) /system/bin/sh: /data/local/tmp/androidvncserver: not executable: 32-bit ELF file
Any clues?
Thanks.
LikeLike
Many phone/tablets require binary executables built for the ARM instruction set. ARMv2 is one target of the C++ compilation process where the final binary is written for that specific processor. It sounds as if the androidvncserver binary should be built for the processor type of your device. This would explain some of the problem but does not explain why you cannot write. Test out some android ADB tools and in setting them up, perhaps the other issue will reveal itself.
LikeLike
Ah, mea culpe (slightly).
I copied the wrong executable – amazing what happens when you follow the instructions!
Mind you, the destination path update still stands (device /data/local/tmp).
But when I execute with adb shell…
(4.2.2)
Initializing framebuffer device /dev/graphics/fb0…
xres=900, yres=1440, xresv=928, yresv=4320, xoffs=0, yoffs=0, bpp=32
Initializing keyboard device /dev/input/event3 …
Initializing touch device /dev/input/event1 …
cannot get ABS_X info, Invalid argument
(5.1.1)
error: only position independent executables (PIE) are supported.
—-
The latter seems to be as per a previous comment from David, so how can I build with PIE enabled?
Thanks (again)
LikeLike
we are writing at the same time. Its good to document issues because they make the trail easier to follow. You are close, just need to find the mouse and touch inputs.
LikeLike
Sorry – stupid here again.
With the instructions from *this* page (!), my android (4.2.2) device works with:
adb shell /data/local/tmp/androidvncserver –t /dev/input/event1 –k /dev/input/event4
For 5.1.1, I modified Android.mk to add the following to enable PIE:
LOCAL_CFLAGS += -fPIE
LOCAL_LDFLAGS += -fPIE -pie
rebuilt, copied, chmod.
When I now execute any variations with adb shell, I get the following (as per Chris):
WARNING: linker: /data/local/tmp/androidvncserver: unused DT entry: type 0x6ffffffe arg 0x11ec
WARNING: linker: /data/local/tmp/androidvncserver: unused DT entry: type 0x6fffffff arg 0x1
Initializing framebuffer device /dev/graphics/fb0…
cannot open fb device /dev/graphics/fb0
Thanks!
LikeLike
Stupid would be to not document issues that others will encounter – good trail paving brother.
LikeLike
You have contributed to this documentation, thanks. I don’t know off hand what the “cannot open fb0” is about. I am traveling but when I get to a proper desk, I will setup a virtual android device if I cannot round up a 5.1.1 device.
LikeLike
Just an extra, the “cannot open fb0″ was 5.1.1 on a Samsung.
I’ve tried on another 5.1.1 device, which is still leaving me with trying to hunt down the mouse and touch device issue.
LikeLike
Firstly, thank you for your work.
I’ve tried to build several VNC servers grabbed from all over the net, unfortunately non of them work under my phone with Android 7.1.2. Just got black screen. Touch event is transferred but the injection has high latency and works wired.
I don’t know when it started, but now actually /dev/graphic has 660 permission and owner is system:graphics, so at least no way to directly use the frame buffer unless root.
Now the main-stream way to grab screen is to use the miracast functionality.
Seems we have no chance use the code on android 7+ rootlessly 😦
LikeLike
Android supported Miracast in Android 4.2 (KitKat) and Android 5 (Lollipop). Native support for Miracast was dropped in Android 6 (Marshmallow) and later. In some situations it might be required to use old versions of Android. I did – and turn off automatic software updates. I dont know about the final assessment on android 7+, I am working with the most recent Android Studio and the mobile integration support just released by Microsoft in VS2017 but not Android 7 right now. I am not faced with the same device you are, but if anyone else out there can contribute their assessments it helps us all.
LikeLike
So what’s the ‘Casting’ function in Android now… I mean after Android 6.
I found this application today:
https://play.google.com/store/apps/details?id=info.dvkr.screenstream
It’s open source. I’ll try combine whatever-cast with vnc. 🙂
LikeLike
Hello BRAINABERLE,
I am trying to implement this project. I have some doubt regarding the process.
When I am executing this command ./adb push /home/user/XMLFoundation/Examples/Android/VNCServer/obj/local/x86/androidvncserver /data/ I am getting adb: error: failed to copy ‘/home/user/XMLFoundation/Examples/Android/VNCServer/obj/local/x86/androidvncserver’ to ‘/data/androidvncserver’: remote Permission denied error. How to overcome this?
LikeLike
The androidvncserver binary is not REQUIRED to be in /data/. Any location will do.
LikeLike
Sorry, I am confused and this post seems a bit old. How is this method different from this one which appears to be simpler: https://www.smarthomebeginner.com/setup-a-vnc-server-for-android/
Brian or someone could you please elaborate?
LikeLike
This post is old. Android was fully open source in the beginning as its merely an offshoot of linux. Google Inc. stole it from the public. I was putting VNC into cross platform tools and did successfully implement an android version using this debugging development hack which will require a different screen capture
glimmer of hope in the open source community behind MicroG. I did not look at the link you posted its take me some time to restudy current solutions.At the moment I’m busy with psychedelics when I’m not incarcerated. http://SyrianRue.org/Brian
LikeLike
Hi, Brian
I want to try the but this link http://www.codeproject.com/Articles/37850/XMLFoundation cannot be accessed. Maybe there is another link that can be accessed
Thank you.
LikeLike
First of all, this approach to VNC no longer works in current versions of Android. Its is accomplish by another mechanism of screen capture. That link should redirect to:
https://www.codeproject.com/Articles/37850/XMLFoundation-2
LikeLike